Since cryptocurrency is still so new, it is largely uncharted territory. At this point, it’s clear that the world of crypto, and its underlying foundation of blockchain technology, have seemingly endless possibilities. Including, having your pet mine crypto for you.
What’s less clear is how to regulate and monitor crypto mining activities. In many cases, clever techniques for mining crypto end up turning into illegal mining programs. Here are 9 of the most ingenious ways people have illegally mined crypto.
Illegally Mined Crypto: A Brief Introduction

Here’s a quick introduction to illegally mined crypto. To understand how it works, you need to know how cryptocurrency is generated. Basically, crypto is “mined” when computers solve complex mathematical equations.
Interestingly, crypto mining requires so much computing power that it leads to noticeable spikes in energy usage. This has been alarming to many. In particular, those concerned about the real-world environmental impact of mining crypto.
Beyond that, mining has also opened the door to a new wave of digital scams. Illegally mined crypto is often the result of hackers sneaking malware into otherwise legitimate code. In other cases, illegally mined crypto is the outcome of more material scams, often involving stealing electricity or taking advantage of subsidized electricity.
One way or another, the goal is typically the same. For people looking to illegally mine cryptocurrency, it’s all about recruiting as many resources as possible—usually, resources who belong to someone else—in order to build up huge crypto mining systems.
With all that said, here are 9 real-world examples of illegal crypto mining.
9. Coinhive Cryptojacking

To be clear, this first example isn’t necessarily illegal. But it’s important to include on this list. That’s because many people consider Coinhive the birthplace of illegally mining crypto.
Last year, a company called Coinhive created a code script that could be easily integrated into an existing web page’s code. When Coinhive’s code is added to a webpage, it automatically turns a visitor’s computer into a mining machine. Basically, the code seizes a certain amount of processing power from visitors’ computers and uses it to mine.
Initially, this was seen as a tool for monetizing websites. In particular, it is an alternative to ads. Basically, the idea is that visitors exchange a bit of processing power for being able to access a website. This would theoretically allow websites to monetize without having to display ads.
Despite its promise for digital businesses, Coinhive’s invention quickly gained momentum with hackers. Soon, the idea of embedding code into a website in order to hijack visitors’ processing came to be known as “crypto jacking.” Now, it’s one of the go-to methods for illegally mined crypto.
8. Showtime Anytime Hack

At some point last fall, it appears that someone hacked TV and movie network Showtime. Visitors to the Showtime Anytime site soon started noticing strange code affecting their computers. After some investigation, people discovered that Showtime’s site used a cryptojacking code.
The company quickly and silently removed the code. But it remains somewhat unclear where the code came from. It could very well have been the work of a cryptomining hacker. But Showtime itself could have put it there in order to monetize visits to the site. Either way, this was a relatively high profile example of cryptojacking.
7. Telecom Server Turned Crypto Mine

Tech companies have noticed an uptick in the number of attempts to hijack the computing power of servers to turn them into huge crypto mines. In fact, recent reports showed that such attempts have increased by six times over the past year or so.
One example of this came last year. An employee at a large telecom company was caught trying to transform his company’s server—which would have immense processing power—into a massive crypto mine.
6. Fake CVs

In an interesting spin on cryptojacking, a malicious miner used infected Word documents. According to news sources, the miner disguised a cryptojacking code as a CV.
Basically, people would download and open the file. And when they did, the code secretly hijacked the computer. The malicious code then used a portion of the computer’s processing to mine coins for the secret hacker.
5. Japanese Cryptojacking Ring

Earlier this year, authorities in Japan discovered a rash of cryptojacking activity. In particular, officials cracked down on 16 hackers. Each of them had embedded some sort of cryptojacking code into a variety of different websites.
These sites reportedly included adult sites and music sites. The hackers also used a number of gaming sites.
This was an interesting legal test case. Specifically, it raised questions about how to police and adjudicate this type of activity. Ultimately, Japanese authorities arrested three of the 16 hackers.
4. Fake Chicken Farm

This attempt at illegally mined crypto has less to do with hacking and more to do with real-world infrastructure. In some parts of South Korea, the government reportedly subsidizes electricity costs for certain industries in order to boost economic activity.
Chicken farming is one of the industries with discounted electricity. Earlier this year, authorities discovered a fake chicken farm. Whoever ran the operation had apparently applied to open a farm and had been using the discounted electricity to run a huge cryptomining operation.
3. The Pirate Bay
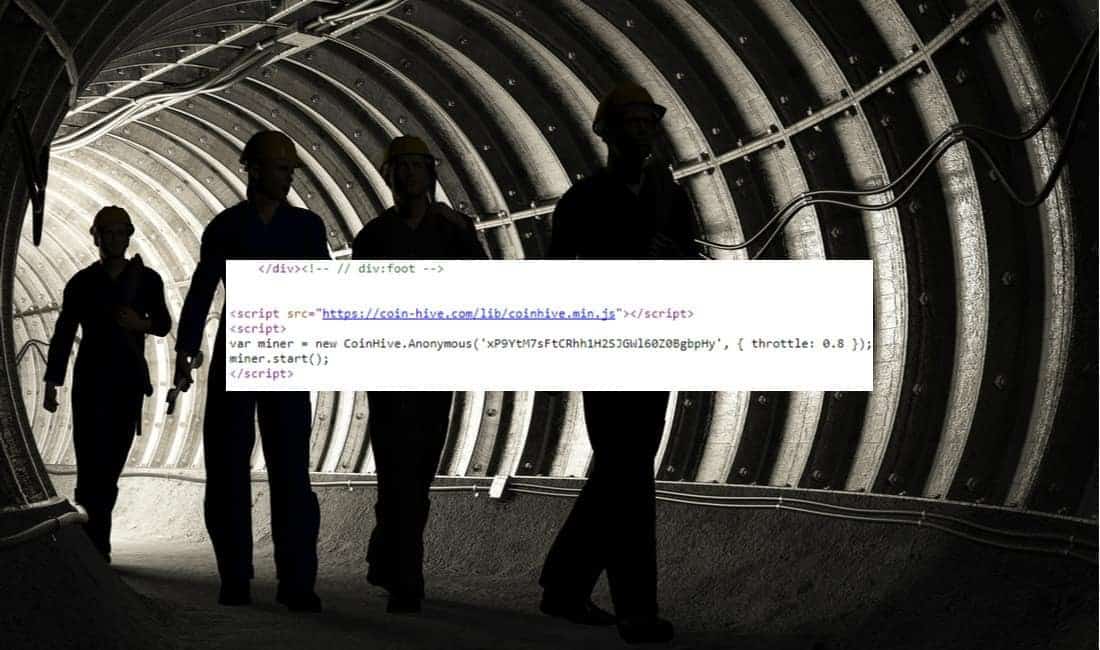
Last year, news broke that The Pirate Bay had embedded a cryptojacking code into its backend. As a result, visitors to the popular but illegal file downloading site were being pulled into a vast cryptomining operation without their consent.
The site reportedly claimed that it was simply trying to monetize its services. But this claim was seen as dubious by many, especially since the site itself is primarily used for illegal downloads.
2. Viral Mobile Game

In the fall of 2017, Forbes reported that a viral mobile game called “Puzzle” was apparently using a hidden cryptojacking code. Somewhere around 10 million people downloaded the game.
Russian developer Alexey Khripkov created the game. When users discovered the code, he initially said it was simply a way to monetize his wildly popular game.
But anti-virus companies apparently disagreed. Anti-virus apps started blocking the game shortly after Khripkov added the code. He subsequently removed the cryptojacking code.
This is another interesting legal case. In particular, Khripkov’s game points to the gray area between legally trying to monetize an app and illegally mining crypto without users’ knowledge or consent.
1. Fake Semi-Conductor Factory

This one is similar to the fake chicken farm scheme. For starters, it also happened in South Korea. Similarly, it took advantage of discounted electricity prices. But instead of posing as a chicken farm, this story is all about a fake semiconductor factory.
Basically, a group of miners applied to the government to open a semiconductor factory. The government approved the application. As a result, the group received a 50 percent discount on electricity.
As it turns out, it wasn’t a semiconductor factory. It was a cryptocurrency mine. When authorities discovered the scam, the miners had reportedly mined more than $500,000 worth of Ethereum. Additionally, the group had also produced a large amount of Bitcoin.